- A flaw in Kia’s dealer system allowed for attackers to remotely unlock and start any Kia using just the car’s license plate
- The vulnerability was patched by Kia in about two months
- It’s yet another wake-up call for automotive security in the connected car sector
Kia isn’t having a great couple of years in vehicle security. From the Kia Boys making the world realize there were 5 million vehicles without immobilizers on the market to new pocket-size GameBoy-style devices, it’s never been easier to be a thief targeting Korean cars.
But wait, there’s more.
A new proof of concept released this week—simply called Kiatool—is probably the most powerful attack against any Kia we’ve seen yet. And, frankly, this one is probably the scariest, too. Thankfully, it’s already been patched, but I want you to hear about it anyway because it tells an extremely important story about the future of automotive cybersecurity.
Meet Sam Curry. He’s one of my favorite security researchers who focuses on the automotive sector. And he has a special knack for breaking into cars. Not by brute-forcing a window with a hammer, of course, but by using some carefully crafted keystrokes to achieve the same effect. Today’s victim was “pretty much any Kia vehicle made after 2013.”
His latest attack takes advantage of Kia Connect. For those unfamiliar, that’s the connected service that pairs a vehicle with the internet so an owner can conveniently unlock their car or turn on the heat when it’s cold outside. With a bit of studying, Curry was able to figure out how to hack into virtually every single connected Kia sold in the United States over the last decade—and only took about 30 seconds.
Have a look at a demo of the tool in the video below:
You’ve Gotta Be Kia’dding me
Let’s dig into what’s going on here. What is being exploited, and how was it found?
Ultimately, the attack boiled down to a flaw in Kia’s Application Programming Interface. An API is essentially an intermediary which allows two applications to talk to one another without exposing certain functions of one app to another. It’s how your car can display your Spotify playlists or pull in traffic data to overlay on its maps.
Curry, as curious as ever, wanted to know how Kia’s app talked to its cars. In short, it assigns an authenticated user a session token (think of it like a virtual permission slip that’s only valid for a short amount of time) that permits them to send commands to Kia’s servers, which then pushes the action down to the car in real life. How could Curry get one of these permission slips and keep it long enough to perform an attack on the vehicle?
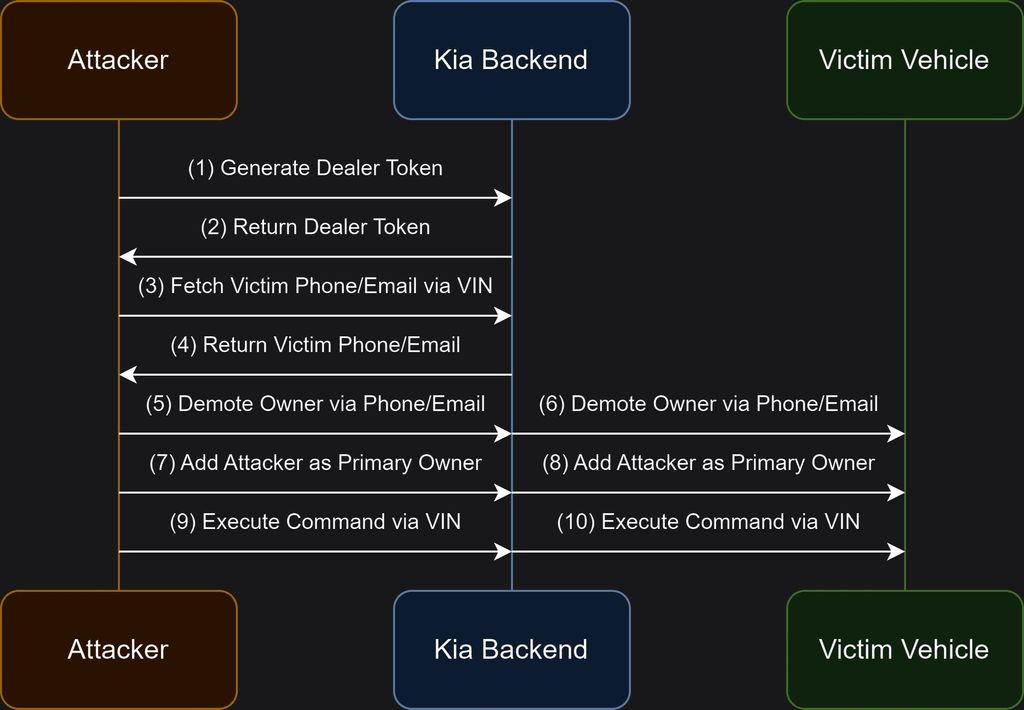
That’s when Curry figured out he could take advantage of the method that dealers use to assign new cars to owners using Kia’s KDealer platform. Curry used a flaw found in the KDealer API which allowed him to impersonate a dealership looking to register a customer’s car.
Next, Curry was able to use a third-party API to pull the victim’s car’s Vehicle Identification Number (VIN) using a license plate, similar to getting a quote for your used car and entering your plate number instead of the VIN. The VIN could be coupled to the forged dealer request and voilà. Instant remote access to virtually any of Kia’s nearly 20 models produced over the last decade.
You’re Exposed
There’s a couple of issues here. First is the glaring threat to the vehicle itself. I mean, let’s cut right to the chase—you can unlock and start the car with just the license plate. That… really bad. Like a relay attack on steroids. And it could all done without the owner ever noticing a thing (except for an eventual missing car or belongings).
Even scarier is the privacy issue at play. The exploit allows the attacker to fetch information about the owner’s name, phone number, email address, the location of the vehicle, and, in some cars, even allows the vehicle’s cameras to be accessed remotely.
In theory, this would allow for an attack chain that lets a driver pull up to a car at the grocery store to get the plate, silently add a burner email account to the owner’s Kia account, find its location later on, then check the cameras to make sure nobody is around when they want to snatch it. Or, worse, use it to target the owner. Scary stuff.
The Hole Is Plugged
The good news is that Kia has already fixed the problem and that the automaker had confirmed that it hasn’t been used maliciously in the wild. Phew.
Like any good security researcher, Curry ethically disclosed this flaw to the automaker when he discovered it back in June. Kia’s developers patched the flaw about two months later in mid-August, and Curry gave it another month before he disclosed the findings publicly yesterday.
The real lesson here isn’t that about Kia’s flaw, as impressive as it was, but is about connected cars in general. It’s a reminder that when something is addressable on the internet, a flaw can translate into real world consequences quite easily.
We, as a society, have become a bit numb to cybersecurity-related events. You hear about ransomware frequently, about leaked social security numbers. It’s becoming mundane. But give an attacker a virtual coat hanger to pop you car’s door lock using their cell phone and things become a bit more…tangible. And that’s scary.
Recently, a group of hackers has discovered a serious vulnerability in the key fob system of Kia vehicles that allows them to gain access to the car and start the engine using only the vehicle’s license plate number. This alarming security breach raises significant concerns about the safety and security of Kia vehicles on the road.
The hackers, who go by the name of ‘The Key Boys’, have been able to exploit a flaw in the key fob technology used by Kia vehicles to remotely unlock and start the engine of the car without the need for physical keys. By intercepting the signals sent between the key fob and the car’s security system, the hackers are able to replicate the key fob and gain unauthorized access to the vehicle.
This discovery has significant implications for Kia drivers as it means that their vehicles are vulnerable to theft and unauthorized access by cybercriminals. With just a license plate number, hackers can potentially gain access to any Kia vehicle and drive away without detection. This poses a serious threat to the safety and security of Kia owners and their vehicles.
In response to this security breach, Kia has released a statement acknowledging the vulnerability and reassuring customers that they are working on a fix to address the issue. The company has advised Kia owners to be vigilant and take precautions to protect their vehicles from potential hacking attempts.
It is essential for Kia owners to take steps to safeguard their vehicles against cyber threats. This includes regularly updating their vehicle’s software, disabling keyless entry systems when not in use, and investing in additional security measures such as steering wheel locks and car alarms.
In conclusion, the discovery of this vulnerability in Kia’s key fob system is a wake-up call for the automotive industry and consumers alike. It highlights the urgent need for enhanced security measures to protect vehicles from cyber threats and ensure the safety and security of drivers and their vehicles on the road. It is imperative that car manufacturers prioritize cybersecurity and invest in robust security systems to prevent hackers from gaining access to vehicles through sophisticated cyber attacks.

